cloud
-
Mitigating Human Errors in Cloud Environments: Executive Guide to Training and Automation
By Andrea StansburyOctober 29, 2025 In our previous blog post, “The Human Factor: Top 7 Human-Generated Vulnerabilities in 2025 and How to Secure Them,” we explored the critical role that human actions play in exposing cloud environments to risks. From phishing susceptibility to unauthorized credential sharing, these vulnerabilities underscore a persistent challenge: even the most…
-
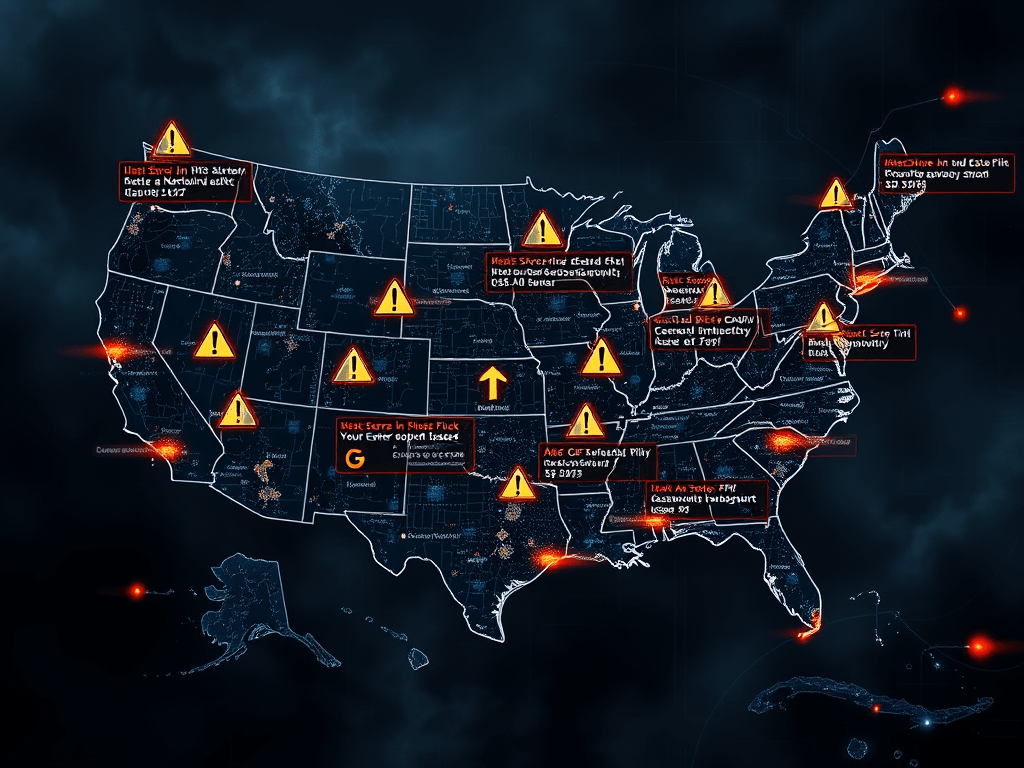
Overview of the AWS US-East-1 Outage
On October 20, 2025, Amazon Web Services (AWS) experienced a significant outage in its US-East-1 region (Northern Virginia), which disrupted multiple services and affected numerous dependent platforms worldwide. This event, occurring in the week of October 15-21, 2025, highlighted the interconnected nature of cloud infrastructure, as issues in a single region cascaded to impact global…
-
Securing Identity and Access Management (IAM) in Multi-Cloud Environments
In today’s interconnected digital landscape, multi-cloud environments have become a cornerstone for organizations seeking scalability, flexibility, and resilience. However, the complexity of managing identities and access across multiple cloud platforms introduces significant security risks. Week 1 of our 2025 cybersecurity focus highlights how executives can enhance security by implementing centralized Identity and Access Management (IAM)…
-
Five Practical Steps to Boost CMMC Level 2 Compliance in a Cloud-Hosting Environment
For organizations pursuing Cybersecurity Maturity Model Certification (CMMC) Level 2, achieving compliance within a cloud-hosting environment can feel daunting. However, by focusing on high-impact actions, businesses can make significant progress toward certification in just 30 days. Below are five practical steps that organizations can implement, along with tools and strategies to streamline the process. 1.…
-
Securing Multi-Cloud Environments: Why MFA is Non-Negotiable for Enterprise Network Admins
As a network administrator overseeing a multi-cloud enterprise setup—spanning AWS, Azure, Google Cloud, and beyond—you’re the gatekeeper of vast digital estates. One compromised admin account can unravel your entire infrastructure, leading to data leaks, ransomware lockdowns, or worse. Enter multi-factor authentication (MFA): the simple yet powerful defense that’s become the cybersecurity equivalent of locking your…